The increasing threat of cybersecurity attacks has led to a strengthening of information security programs across all industries. The transit industry is no different, but the cyber hygiene of the technology supply chain remains a soft underbelly of many security programs.
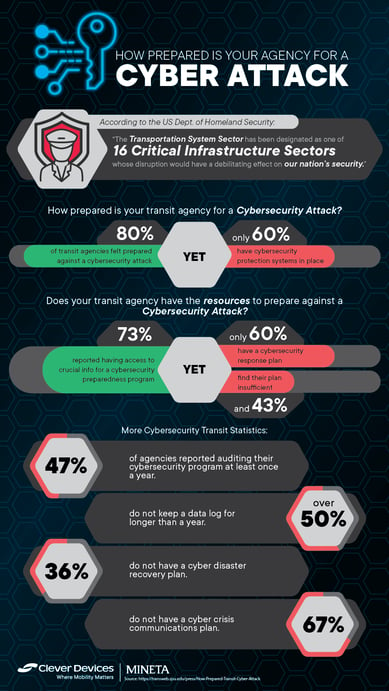 The U.S. Department of Homeland Security has identified the transportation industry as one of 16 critical infrastructure sectors whose assets, systems, or networks are so vital to the country that their incapacitation would prove debilitating to the nation’s security, economy, or public health and safety. As the world grows ever more connected, the risk of bad actors initiating a cyber attack on critical infrastructure like transit becomes an inherently larger threat. The FBI's Internet Crime Complaint Center reported a 62 percent increase in ransomware complaints in the first six months of 2021 compared to the same time frame in 2020. Some of the most notable ransomware attacks in recent years have involved large and small public transit agencies.
The U.S. Department of Homeland Security has identified the transportation industry as one of 16 critical infrastructure sectors whose assets, systems, or networks are so vital to the country that their incapacitation would prove debilitating to the nation’s security, economy, or public health and safety. As the world grows ever more connected, the risk of bad actors initiating a cyber attack on critical infrastructure like transit becomes an inherently larger threat. The FBI's Internet Crime Complaint Center reported a 62 percent increase in ransomware complaints in the first six months of 2021 compared to the same time frame in 2020. Some of the most notable ransomware attacks in recent years have involved large and small public transit agencies.
Despite the alarming headlines and words of warning from multiple government agencies, a recent Mineta Transportation Institute report found that despite over 80% of agencies feeling prepared for a cybersecurity threat, only 60% had a program in place to mitigate such threats. However, there are a growing number of resources to help agencies establish the appropriate cybersecurity infrastructure and develop a game plan for vetting vendors and third parties. For example, some FTA grant programs can be utilized to develop cybersecurity programs, including FTA’s Urbanized Area Formula Program, the Formula Grants for Rural Areas Program, and the State of Good Repair Program.
The RFP process provides an opportunity for a transit agency to dictate information security expectations to their potential technology vendors. Yet, it is a process often used with varying degrees of success. Some RFP specifications provide little to no mention of cybersecurity, some specifications contain boilerplate language that often does not apply to the system being procured. Further, some specifications over-prescribe security requirements, resulting in costly and time-consuming project development and deployment schedules.
 Explore our Cybersecurity
Explore our Cybersecurity
Resource Hub
Looking to learn more about how your agency can get ahead of potential cyber-attacks and better evaluate the cybersecurity hygiene of potential vendors and ITS providers? Check out the Cybersecurity resources Clever Devices has made available for transit industry professionals, including a handy checklist for agencies vetting third-party vendors during the ITS procurement process. Access the Cybersecurity Resource Hub here.